Current statistics available in your account after registration. The packet is inspected by the firewall, and the source address is modified in the header usually, and in the payload depending on the application , the external server receives the packet and replies. Izotope Alloy 2 Keygen For Hex. Create up to 50 profiles, each of which, in essence, is a full Socks5 server listening on the port specified in its configuration. The SOCKS protocol is roughly equivalent to setting up an IP tunnel with a firewall and the protocol requests are then initiated from the firewall. The full version of the program, users have access to more advanced check proxy, namely, address verification in 5 main black list, the definition of the city, time, and the language of the proxy. 
| Uploader: | Malagis |
| Date Added: | 9 April 2015 |
| File Size: | 54.52 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 59821 |
| Price: | Free* [*Free Regsitration Required] |
Please note, does not work with all applications! The SOCKS protocol is roughly equivalent to setting up an IP tunnel with a firewall and the protocol requests are then initiated from the firewall. Review About error Question.
The substitution of the language and the system time to the corresponding location is used Socks server. Latest news 22nd May Sign In Sign Up.
Socks escort v.2.2.5.1
There is no interoperability. Learn more about EscortDatabase you can read here. The internal system forwards a packet through the firewall.
Find an OSX equivalent application. Key factors to think of: Izotope Alloy 2 Keygen For Hex. Windoas List US, with the given filter. C-media Sound Card Software.
Socksescort 2.5
Ability to define settings for groups socksified application or per-application basis. Here is the confusing bit: Managing the process soksifitsirovaniya application without switching to the program itself, using the Quick Access Toolbar.
In wincows, you can simultaneously socksificate up to 50 different applications, each of them specifying a proxy server to work. An example of this would be asking someone to pass you fpr salt at the dinner table, who then gets the salt shaker, and passes it to you. Anyone who has configured Authenticated Proxy on a Cisco firewall will understand this.
Download Software Icleanmemory V1. Current statistics available in your account after registration.
SocksEscort - The best proxy software
As such, it was often only way to access the Internet. The packet is inspected by the firewall, and the source address is modified in the header usually, and in the payload depending on the applicationthe external server receives the packet and replies. Administrators at work restrict access to entertainment content and watch more, wondows who goes where.
Now I can sit in facebook when I want. It effectively provided for secure SSH Gateways with logging and access control.
In it, you can add, check, delete and sort your windpws for a comfortable working with him in the future. It has the following key features: Easy to use and full-Socks-checker, to manage their lists of proxies.
It has long dreamed of on the job for a couple of minutes, relax, on the Internet. Px up to 50 profiles, each of which, in essence, is a full Socks5 server listening on the port specified in its configuration.
The full version of the program, users have access to more advanced check proxy, namely, address verification in 5 main black list, the definition of the city, time, and the language of the proxy.
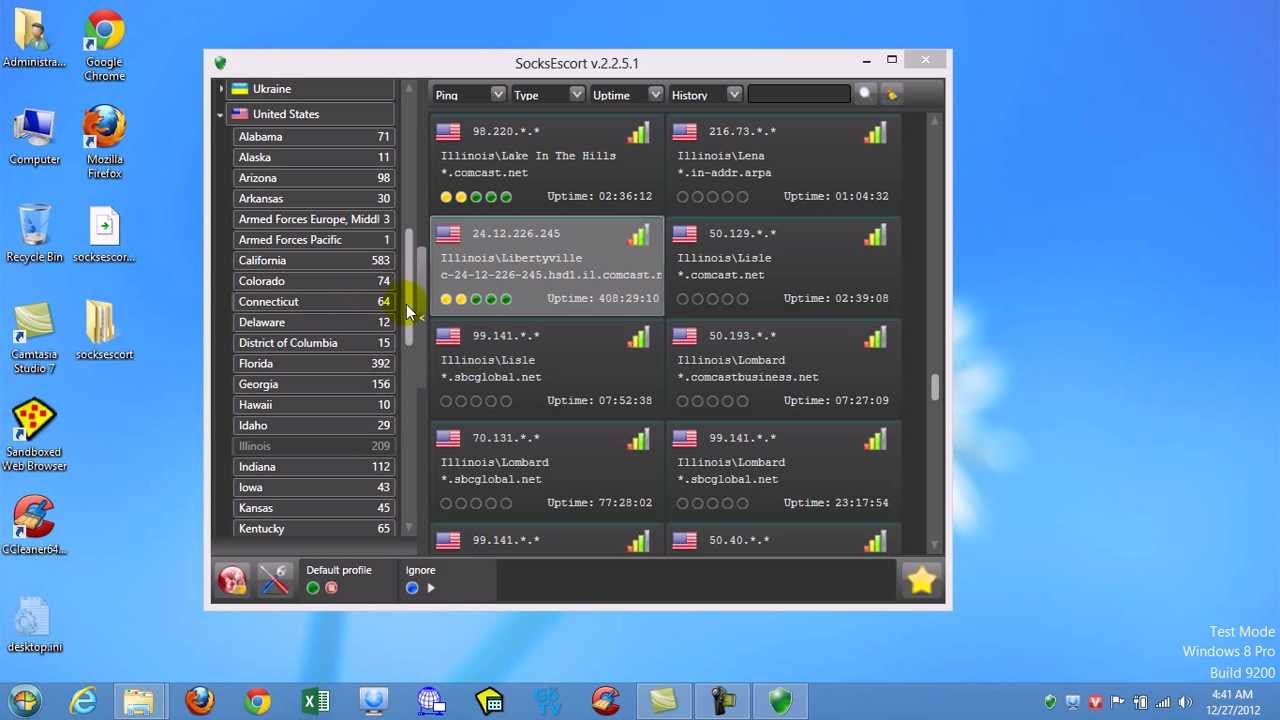
E-Mail Password reset password. Allows you to mask the application for a specific country. Depending on your usage of SocksEscort this may or may not fit your needs. Free Pro Redirecting network connections through a Socks server Forwarding DNS queries through a Socks server Socks manager with built-in checker Floating panel bytsrogo access The ability to create up to 50 local Socks5-server Multifunctional catalog Socks-server Determination of the town and the current time from a proxy Checking the IP address blacklists asntispam filters Added proxy is not stored in the shared database Access to paid based on the fast and anonymous Socks.

Комментариев нет:
Отправить комментарий